INTERODUCTION TO E-MAIL
Electronic-mail or E-mail is the process of sending messages anywhere electronically using the computer and a modem. Email can be sent and received according to the convenience of the user. Any number of Emails can be sent at a time to any number of designated locations. E-mail is delivered almost instantaneously. E-mail is cheap and easy to use especially for international messages. The cost of an E-mail is only the price of the telephone connection to the Internet Service Provider.
WHY USE E-MAIL?
- It is much cheaper to send an E-mail than a letter.
- It is much cheaper than a long distance phone call.
- It saves paper and raises productivity within the office environment.
- Replies can be formulated at leisure and are easily sent (no searching for addresses).
WHAT IS AN EMAIL ADDRESS?
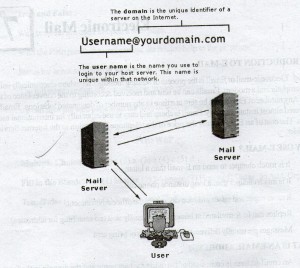
An email address is composed of two parts the user name and the domain in the format username@domain. Each email address uniquely identifies an Internet user.
The user name is the name you use to login to your host server. This name is unique within the network. The domain is the unique identifier of a server on the Internet user.
EMAIL NETWORKS:
Email Networks are nothing but a group of users who share common information with the help of emails. One can become a part of network by signing on to the network. After which one will receive or post queries or information to the user group or the email network.
WHAT IS A MAIL SERVER?
Mail server is software residing on the server that acts as a collection point for incoming and outgoing E-mail for the users that it services. While the mail server will route outgoing E-mail upon receiving it from the user, it will store incoming E-mail till the user’s mail client requests it to be downloaded and then deleted.
WHAT IS SMTP?
SMTP stands for Simple Mail Transfer Protocol. This protocol is a server-to-server protocol that usually operates in the background, and is the standard way in which mail is transported over TCP on port 25. SMTP simply routes the messages from one mail server to another.
WHAT IS POP3?
POP3 is Post Office Protocol, version 3. It is an email protocol that all allows a user to read and delete mail from the server. It differs from IMAP in which it does not allow email to be manipulated on the server, but requires mail to be downloaded onto the client computer.
POP3 is better suited for the average user using a single computer. POP3 matches the method used by most users to use email: download, read, delete. In contrast, IMAP, reads, sorts, and makes email available for download. IMAP allows the user to easily download messages from his account by eliminating the need to manage the account size.
WHAT IS MIME?
MIME stands for “Multipurpose Internet Mail Extensions”. It is the standard for how to send multi-part, multimedia, and binary data using the world-wide Internet email system. Typical uses of MIME include sending images, audio, word processing documents, programs, or even plain text files.
WHAT IS IMAP4?
IMAP4 is a protocol for reading mail messages from a mail server over a network.
How does it work?
IMAP4 was designed to make it easy for users to manage reading their e-mail from more than one location or over a slow Internet connection. Unlike POP3, which generally downloads all mail messages in a user’s mailbox at once, IMAP4 only downloads message headers form the mail server. The main body of the mail messages and the attachments reside on the mail server until requested. Once requested, the entire message is copied from the mail server and sent to the user. All mail is stored on the mail server until the user deletes and purges it. IMAP4 provides only header information so that the user’s computer does not download all mail at once. By giving the user the option to request only the messages they want to read, IMAP4 helps mobile users save time in downloading and reading mail over slow links.
Users can also create multiple mail folders on the IMAP4 mail server and move messages between the folders. By keeping all messages on the mail server, users can log into the IMAP4 server from different locations and have access to both new and old messages in their mail folders.
Benefits of IMAP4:
– Mail is centrally stored and managed on the mail server and can be backed up.
– Users can access mail from any IMAP compliant computer.
– Users can choose the messages to download.
– Users can retrieve messages form the server if they have accidentally deleted the mails. This is possible only is the user has not delete and purged the mails.
EMAIL HEADERS.
Emails have headers that provide information on the origin of a message and enable you to track and stop junk e-mail. Most e-mail clients only show the To: and From: headers, which can be easily forged. The complete massage headers will look something like this:
Return-Path: [fake@adress.com]
Received: from some.host.com (hostname [xx.xx.xx.xx])
by mydomain.com (8.9.3/8.9.3) with ESMTP id NAA 123456;
Thu, 11 May 2002 10:15:30 + 0530 (EDT)
Date: 11 May 2002 10:15:30 + 0530
From: Spammer [junk@mydomain.com]
To: user@mydomain.com
Subject: My junk message!!
Netscape Mail (ver 4)
Click View from the pull-down menu bar. Then click Headers and Select all.
Outlook Express
Open the message. Then click File from the pull-down menu bar and selected Properties. Another window with two tabs is displayed. To view the details, click the Details tab. Cut and paste the headers into the message that you want to forward.
EMAIL STRUCTURE
To: In this field you can type an address (or several addresses separating names with a comma or semicolon) to whom one would like to send a email to.
CC (carbon Copy): This will send a copy of the message to the address placed in this field and other recipients can see that the copy was sent.
BCC (Blind carbon Copy): This will send a copy of the message to the address placed in the field but other recipients do NOT see that the copy was sent.
SUBJECT line: The subject should be should be short but descriptive. Some people filter their mail by subject so the subject line should be reflective of the contents of the message or the message may not be read by the recipient
EMAIL STRUCTURE
(Body): You can type your message in the message field, copy text from another program and paste in the message field or embed a document in the message field. Notice that the font options (color, size, style) become active at this point. REMEMBER the recipients of your message using a different email program may not see text the same way you wrote it.
Attachment: This a feature allowed in a email to attach other files and documents such as text, audio, video sound.
WHAT IS A MAIL CLIENT?
A mail client is a specialized program that is designed for checking and composing email. There are several freely available mail clients including the open source Netscape mail and the Microsoft Outlook Express.
Advantages of mail client.
When using a mail client, you do not have to be connected to the Internet. You can connect, download all your email, disconnect, and read the emails when you want. This is a very nice ability you use a modem at home and have one phone line. Also, you can compose email anytime, save it, and send it later when you are connected to the internet.
Mail clients provide more features than web mail; such as integrated spell checking which identifies misspelled words, powerful address books, and mail filters. Mail clients are faster than web mail. When you access mail by using web mail, you have to wait for the web server to generate the next web page and send the page over the internet every time you click a link or button. In contrast, mail clients are applications on your computer, so the interface responds quickly to your commands. Some mail clients allow you to check and send email from multiple accounts from one place.
There are also some disadvantages in using the mail client:
To use a mail client, you must install software on your computer and configure specific accounts. If you are using a computer at a public place, you will not be able to use a mail client.
A mail client stores mail on your machine. This may be a concern if you want to keep your communication private. Mail clients are often more difficult to learn how to use.
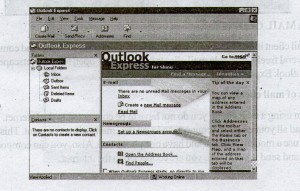
OUTLOOK EXPRESS:
Using Outlook Express: Click on the Outlook Express icon on the desktop or click on the START button at the lower left of the screen and then select Programs/Outlook Express.
The list of folders contains folders for:
Inbox: Contains a list of incoming mails received by the user
Outbox: Contains a list of mails that was composed offline and is ready to send and messages that you elect to send later
Sent Items: Contains a copy of messages that one has sent
Deleted Items: Deleted items are temporarily stored here. Right click on the deleted folder and select to empty it.
Drafts: These are messages composed but which are not ready to be sent
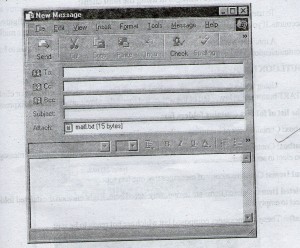
SENDING MESSAGES:
Click on the send button to send this message.
Start a new message:
On the toolbar, click the New Mail button. Select the address of person to send to.
Type the subject
Attachment: To attach a file click on the attach icon and them attach the file.
Type the your message.
Click on the send icon. The message will be sent.
WEB MAIL
Allows you to send and check your e-mail by logging in to a user-friendly web-based interface, similar to that operated by Hotmail. This can be particularly useful when away from your home or office. This feature allows you to access your mail from anywhere you can access the web. All you need is a computer connected to the Internet and a web browser
NETSCAPE MAIL
Netscape mail is a mail client from Netscape. It has similar features of Internet Explorer. Like Inbox, Outbox, Draft, SentItems.
It also has features of creating mail accounts so that one can download mails.
Almost all the features are similar to Outlook Express
EMAIL ENCRYPTION
Encryption of email messages is absolutely necessary, if you send sensitive, personal, or business information through an open network such as the Internet. Unless you have been a meditating hermit for the last few years, the media has bombarded you with the woes of sending unencrypted email. Still, 99% of all email traffic travels though the Internet unsecured.
An unencrypted e-mail can go anywhere for that matter. It all depends on the state of Internet “traffic” that day. An e-mail message can pass through numerous different computer systems en route to its final destination. Meanwhile, on some computers though which those e-mail is relayed, there may be ‘sniffers’ or other malicious software tools. They are waiting to copy, alter or tamper with that e-mail in some way. Some are looking for key words or manes. Other sniffers are watching for credit card numbers or login passwords.
Email Encryption is the conversion of information (data) into code, to ensure confidentiality. Email encryption, then, is encoding email messages so that only the intended recipient(s) can read them.
DIGITAL SIGNATURES
Most e-mail encryption tools have another element. On top of encryption algorithms, they add a digital signature. The digital signature assures the e-mail’s reader that no one tampered with the message and that it did in fact come from the author.
To do this, a digital signature combines two pieces of information: a hash and the author’s private key. First, let’s talk about the ‘hash.’ The software creates the ‘hash’ which is a sequence of numbers (ones and zeros) unique to the author’s message. The software does this by first scrambling the message. Think of it like making scrambled eggs and hash browns, mixed up together in the frying pan. Then the software crunches the scrambled mess down, digitally that is now think of crunching the scrambled eggs and hash brown potatoes into a small egg cup. That’s the hash: the stuff that made it into the small egg cup.
The encryption software can only create one possible hash from an original message. However, there could be other messages that end up creating the same hash. Still, finding those other messages are virtually impossible. Though improbable, a person could find a different message that creates the same hash. that other message would most likely be gibberish.
This hash cannot be reverse engineered (that is why they call it a one-way hash). The digital hash is just like the scrunched up hash in the egg cup. There is no way to go backwards. The hash cannot go back to the eggs in their shells and the unpeeled potato. So no one can use the digital hash to find out what the message is, nor can it be used to create a different message resulting in the same hash. The common length of the hash is 128 bits.
The second step is to encrypt the hash. The author encrypts the hash using his/her private key. Voila: a digital signature. The reader can decrypt the encrypted hash using the author’s public key. The intended reader’s encryption software checks to see if the author’s message creates the same hash. That ensures that no one has altered the message.
The digital signatures work the opposite way to ordinary messages. The author encrypts the outgoing hash with his private key. Then the author sends out his/her public key to allow readers to verify the hash is right. The reader would also know that only the author could have initially encrypted and sent the e-mail. Only the author has the private key that will make that system work. The weak link is in the complexity of the keys that a user creates. A safe bet is to have keys with a minimum of 230 digits.